Many businesses operating in Mainland China, whether multinational corporations (“MNCs“) or domestic companies, transfer personal information (“PI“) out of the country in the ordinary course of business. Such outbound PI transfer is governed by the PRC Personal Protection Information Law (“PIPL“) and ancillary implementation rules.
In our previous article published in July 2022 (Cross-border Data Transfer between Hong Kong and Mainland China – What do we need to Know?), we briefly outlined the three routes through which PRC data processors may lawfully export PI, namely by:
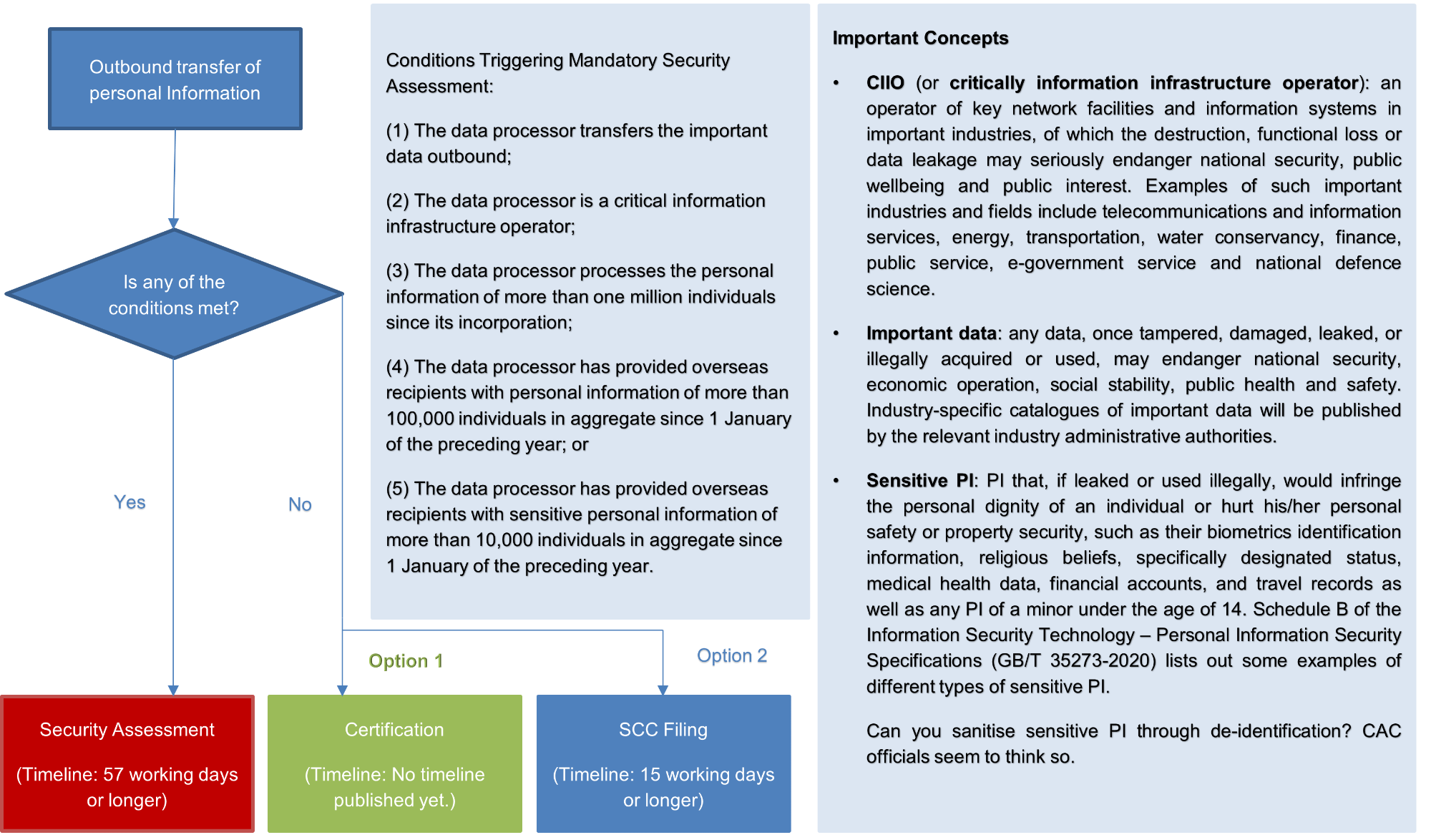
- passing the mandatory data security assessment conducted by the Cyberspace Administration of China (“CAC“) (“Security Assessment route“);
- completing the certification of PI protection by a professional institution (“Certification route“); or
- incorporating standard contract clauses (“SCC“) published by the CAC in contracts with overseas PI recipients and filing such contracts for recordal with the CAC (“SCC Filing route“).
Since then, China has released a series of implementation rules, standards and guidelines for outbound PI transfer[1]. This article updates our readers on the key concepts, procedural requirements and practical implications of different data export routes for sharing PI with overseas recipients.
Scenarios of Outbound PI Transfer
The most obvious form of outbound PI transfer occurs when PI collected and produced in domestic business operations is transferred or stored out of Mainland China. Chinese entities often provide PI to overseas entities electronically, either via software or hardware. For example, a Chinese subsidiary regularly submits operational reports and analyses, including PI, to its overseas headquarters by electronic means.
In addition, members of a MNC group (including the PRC subsidiaries) use the same office administration and HR systems quite often to handle daily business flow and HR data, and the relevant data is all stored and backed up via the cloud server set up by a foreign service provider.
A less obvious form of data export occurs when PI is stored domestically but can be accessed overseas. Similarly, when personal data is collected and generated overseas is transmitted to China for processing, PI re-export occurs when the processed data is sent back abroad.
A more controversial scenario is when an oversea entity, not having any registered presence in Mainland China, directly collects PI from Mainland individuals during the course of providing goods or services to them. Some argue that, since no PI processor within China is involved in such a case, it is not considered an outbound PI transfer as outlined in the PIPL. However, others argue that the outflow of PRC-sourced PI obliges the overseas PI processor to appoint a Mainland representative to apply for the Certification route. In this regard, the text of the PIPL contemplates that cross-border transfer of PI only occurs when a PI processor provides PI to any party outside Mainland China, thus is more in line with the former view.
Which Route to Take?
Below is a chart summarizing how to decide which path to choose in order to transfer PI overseas.
As shown in the chart, if the data processor is either a critical information infrastructure operator (“CIIO“, as defined below) or processes PI in an amount exceeding the threshold specified by CAC, such data processor must go through the Security Assessment route.
Where companies are not subject to the Security Assessment, they can choose either the SCC Filing or Certification as a pathway to transfer PI overseas.
It should be noted that prior and separate consents by the data subjects are required for an Outbound PI Transfer.
Prerequisite for each data export route: PI Protection Impact Assessment
For each data export route, a PI processor must complete a personal information protection impact assessment (“PIPIA“) to evaluate the legality, legitimacy and necessity of the intended data transfer, the relevant risks and the scope and methods of the PI processing and protection efforts by the exporting processor and the overseas recipient. In other words, PIPIA is for validating compliance of data processing activities, identifying risks that may prejudice the data subjects’ legitimate rights and interests, and evaluating the effectiveness of various data protective measures.
A PIPIA must be completed within three months prior to the filing date of each PI export route, and the resulting report must be included in the filing package for each route. The statutory guidelines for Security Assessment and SCC Filing each includes a template PIPIA report. The two templates have some overlapping provisions, with SCC Filing covering more expansive aspects, such as the processing of sensitive PI while the PIPIA report template for Security Assessment puts more emphasis on the impact on and protection of national security and public interest.
The PIPIA report templates require some information of the overseas data recipient(s), including their basic information, usage and methods of data processing, data security protection capability, description of the entire data processing cycle etc. It is therefore important to allow sufficient lead time for back-and-forth communications between the PI processor and overseas recipient before finalizing the report.
As PIPIA is a self-evaluation process, it can take 3 to 6 months depending on the PI processor’s own situation. PIPIA reports have to be kept for at least three years.
Security Assessment
In addition to doing a PIPIA, an exporting data processor subject to Security Assessment must also assess the risks with the proposed data transfer. In practice, as there are overlaps between the PIPIA and the risk assessment, the risk assessment can be prepared and supplemented based on a PIPIA report.
The application for Security Assessment shall be submitted to the CAC through its provincial counterpart. The lack of clarity of the review criteria may slow down the review and approval process.
Given the long processing time, an exporting data processor should ensure it will only become bound to share data with the overseas recipient upon completion of the Security Assessment. Security Assessment results are valid for two years.
It appears from the news that most applicants for Security Assessment are from the e-commerce platforms, health care, aviation, automobiles, finance, logistics, security, and communications industries.
SCC Filing
A PI processor should, within 10 working days of its effective date, file the SCC and a PIPIA report for recordal with the local provincial-level CAC. The outcome will be either a “pass” or “fail”. An applicant which fails to pass the SCC Filing has to provide supplementary information and documents. This makes the SCC Filing more like a de facto approval rather than a mere formality. It remains to be seen what level of scrutiny the provincial-level CAC will exercise in the review process.
Compared with the Certification route, the SCC Filing route offers greater time and cost efficiency. It is anticipated that most eligible applicants for the SCC Filing will be small and medium-size enterprises, and its application scope will be limited to the transfer of PI or sensitive PI within the threshold.
It is reported on 25 June 2023 that a Beijing-based data processing company passed the first-ever SCC Filing with the Beijing CAC just 15 working days after the SCC regulations become effective. The overseas data recipient in Hong Kong, in this case, is an indirect shareholder of the Beijing company.
As the grace period under the SCC rules will expire at the end of November 2023, it is likely there will be more SCC filings in the next few months.
Furthermore, for cross-border transactions involving two-way transfer of PI, both contractual parties need to comply with the data privacy laws of the countries where they are incorporated or operate. This often creates an additional hurdle to the transaction, particularly arising from negotiation and execution of the SCC. How to negotiate a valid and agreeable contract will then become a critical issue for cross-border investment and M&A transactions.
Certification
Compared with SCC Filing, Certification, by which the data processing activities that a PI processor conducts are certified compliant with the standards, has the advantage of covering multiple data processing scenarios and overseas recipients. However, the processing time will likely take longer than the SCC route. MNCs with subsidiaries in Mainland China which regularly transfer PI to their overseas affiliates may want to consider this route.
The specific procedures of Certification involve acceptance of certification engagement, technical verification and/or onsite inspection by the certification institution.
The China Cybersecurity Review Technology and Certification Centre (“CCRC“) is reportedly the only institution authorized to conduct the Certification so far.
A Certification certificate will be issued with a validity of three years. The certification mark for PI protection that includes cross-border processing activities will also be granted, which can be used by the PI processor in advertising and other publicity.
No successful Certification case has been reported so far as of the date of this article.
Outbound Data Transfer in Response to Investigation of Legal Action of Foreign Jurisdiction
According to Article 36 of the PRC Data Security Law (“DSL“), any data stored within Mainland China cannot be provided to foreign legal or enforcement authorities without competent Chinese authorities’ approval. This restriction applies to all types of data, including PI. The PIPL also includes a similar provision (Article 41), which prohibits the transfer of PI to foreign judicial or law enforcement authorities without the approval of a designated Chinese authority.
However, neither the DSL nor the PIPL provides further details on the scope of such restriction or the mechanism of seeking approval. As a result, it can be challenging for companies to navigate these regulations and ensure compliance.
Potential to Optimize Transfer Mechanism for MNC’s Cross-border Data Transfer
On 13 August 2023, the State Council released the Opinions to Further Optimize the Environment for Foreign Investment and Increase Efforts to Attract Foreign Investment (the “Opinions“), which aims to further boost foreign investment. Among the 24 policy measures in the Opinions that address the tensions between and MNCs over data security, the State Council recommends exploring convenient management mechanisms.
Specifically, the Opinions proposes the following key measures:
- to explore the establishment of a “green channel” for eligible foreign-invested enterprises to efficiently conduct security assessment for outbound transfer of important data and PI; and
- to support Beijing, Tianjin, Shanghai, and the Guangdong-Hong Kong-Macao Greater Bay Area on pilot basis to formulate a list of “ordinary data” that can flow freely across borders.
The introduction of a list of ‘ordinary data’ that can flow freely brings promising news for MNCs. Specifically, this might mean that human resource data and customer data, which are regularly transferred to global headquarters during routine business operations, would no longer be subject to data export security assessments, the filing of standard data transfer contracts, or personal data certification, as long as they fall below a certain threshold.
While implementation detail has yet to come out, the development is a significant step forward in facilitating international data transfers and reducing regulatory burdens. If the two measures in the Opinions are substantively implemented, enterprises can expect substantial reduction in data compliance time and cost.
Takeaways
China’s data protection and cybersecurity regulatory regime is rapidly evolving and poses significant challenges and compliance obligations for companies conducting business in and within Mainland China.
The outbound PI transfer regulated under current Chinese laws not only includes the scenarios where PI collected and generated within Mainland China is transferred and stored outside of Mainland China, but also includes the scenarios where a foreign entity or individual is granted with the access to or use any PI stored within Mainland China.
It is crucial for companies to closely monitor legislative and enforcement developments in these areas, by preparing proactively for necessary compliance-related actions, and evaluating or re-evaluating which route(s) are suitable and how to minimize risk exposure for the Outbound PI Transfer under the PIPL.
As for overseas recipients of PI, it might be desirable to vet if the PI processor in Mainland China has chosen the appropriate route and completed the necessary application, filing or certification procedures for the Outbound PI Transfer.

[1] These include (i) with respect to Security Assessment, the Security Assessment Measures for Outbound Data Transfer (Data Outbound Security Assessment Methods) and First Edition of the Guidelines for Application of Security Assessment of Outbound Data Transfer (Data Outbound Security Assessment Application Guidelines (No. 1st edition) both effective on 1 September 2022; and (ii) with respect to Certification, Implementing Rules for Certification of Personal Information Protection (Personal Information Protection Certification Implementation Rules) and the Practical Guidance on Cyber Security Standards – Security Certification Specifications on Cross- border Transfer of Personal Information V2.0 (Cybersecurity Standard Practice Guide—Security Certification Specification for Cross-Border Processing of Personal Information V2.0) on 4 November and 16 December 2022, respectively, and (iii) with respect to SCC Filing,the Measures for Standard Contract for the Outbound Transfer of Personal Information and the First Edition of the Guidelines for Filing of the Standard Contract for Outbound Transfer of Personal Information (First Edition of the Standard Contract for Outbound Transfer of Personal Information) Edition), both effective on 1 June 2023.






