23 December, 2019
The article below was extracted from The Monitor newsletter, a monthly digest of Kroll’s global cyber risk case intake. The Monitor also includes an analysis of the month’s most popular threat types investigated by our cyber experts. Subscription is available below:
Kroll identified a variety of SIM swapping incidents via its intake process for cyber investigations between July and September 2019, two of which resulted in access to victims’ financial institutions. Subscriber identity module (SIM)1 swapping is a type of attack in which a malicious actor induces a mobile service provider to cancel the target’s SIM card and then port the target’s mobile phone number to the hacker’s SIM card and phone. The hacker can then use the hijacked phone number to request SMS-based one-time passcodes2 to access the victim’s online accounts, reset passwords, or transfer assets.
One of the hallmarks of SIM swapping fraud is the speed of attacks, says Associate Managing Director Pierson Clair. “Hackers don’t waste time; once the SIM swap occurs, they immediately start accessing the victim’s online accounts, and the financial losses can rack up very quickly,” explains Pierson. He notes that beyond traditional financial accounts, any kind of desirable asset is attractive to these cybercriminals, such as cryptocurrency or customer loyalty rewards (e.g., credit card rewards or frequent flyer mileage).
Pierson notes this efficiency is also reflected in the fact that attackers are generally looking to collect readily available public information in order to carry out the swap (see “How Does a SIM Swap Work?” below)
Accordingly, people with an extensive public footprint whom an attacker assumes to potentially own assets worth pursuing are favored targets. C-suite executives, business leaders and board members, entrepreneurs, and individuals well known in their industry sector or community often fit the bill perfectly.
Recent Kroll cases and federal indictments indicate a significant trend in targeting individuals involved with cryptocurrency investing and trading. These individuals are increasingly becoming victims because it is easier to leverage SMS-based two-factor verification (2FA) to transfer and launder cryptocurrency accounts compared with traditional fiat currency. (See “In the News” section below.)
While attacks themselves are efficient, unfortunately it can take victims a day or more to figure out what has happened and remediate the damage. Some aspects of a SIM swap attack are out of a person’s control (e.g., a network provider employee who mistakenly permits the SIM swap), but Pierson says individuals can proactively take steps to forestall a swap and/or limit damage until they can sort things out with their service provider. These include cybersecurity basics such as avoiding credential reuse across online accounts and taking full advantage of all security features offered by a service provider. Pierson outlines these measures more fully in this newsletter’s Experts Corner.
How Does a SIM Swap Work?
According to Pierson, a SIM swapping attack is primarily a three-step process – identify the target; conduct reconnaissance; then make the swap and drain assets.
- Identify the Target
As mentioned earlier, attackers are looking for high-value targets for whom extensive and accessible data exists. Some of the data can simply be public knowledge (e.g., executives listed on a company’s website), but much is commonly shared by victims themselves (e.g., articles, interviews, or postings to various professional and personal social media platforms). Targets with unusual names make it that much easier for attackers to find applicable data faster and avoid false positive results from their research. - Conduct Reconnaissance
Pierson says the next step for cyberattackers is akin to a background intelligence workup. Drawing on a combination of publicly posted information and dark web sources, bad actors work to glean facts that help with not only the SIM swap, but also later when cracking accounts. For example, if a victim’s email addresses and passwords were compromised in a data breach, that information is for sale somewhere on the dark web. A cursory view of social media postings can often provide more than enough clues for guessing usernames and passwords, as well as answers for common account verification questions (mother’s maiden name, favorite vacation spot, pet’s name, first school, etc.). - Make the Swap and Drain Assets
Once a hacker has collected enough information on a target, they will then leverage either social engineering or an insider at the phone company to conduct the SIM swap operation whereby the victim’s mobile number is changed to point to the attacker’s phone. The attacker can then request one-time passcodes to reset the victim’s online accounts, facilitating access to email, social media, and asset-holding accounts. In cryptocurrency cases, at this point the attacker can transfer crypto assets to a crypto wallet under their control, and then launder cryptocurrencies via various methods available on the dark web.
SIM Swapping with Insiders on the Dark Web
Kroll’s analysis of dark web marketplaces indicates that there is a large volume of advertisement for SIM swapping services available on multiple forums. In most cases, actors are reluctant to talk about their intentions on the forums and prefer to move to peer-to-peer chat applications, such as Jabber or ICQ. However, based on Kroll’s experience, we can assess what these actors are planning or what type of assistance they are seeking. Following are some examples of recent global activity related to SIM swapping.
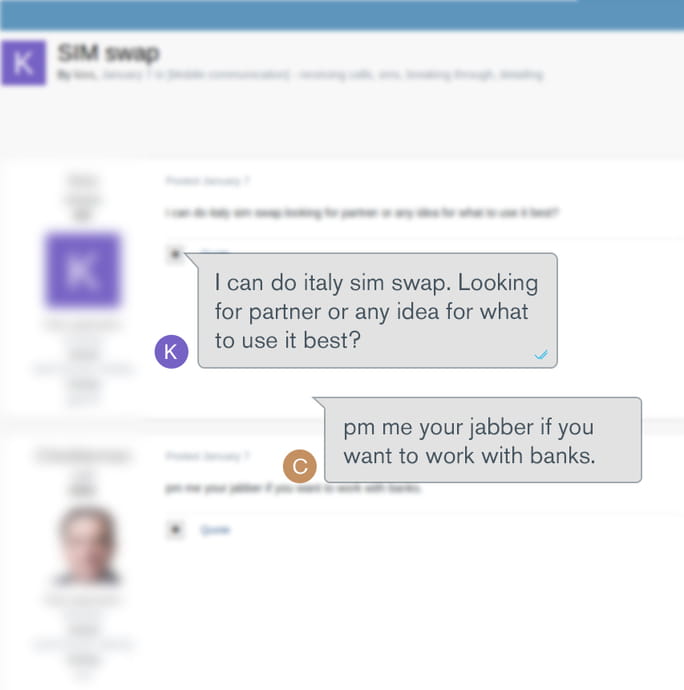
Example 1 – Actors Looking to Expand Into New Geographies
Kroll assesses that in this exchange, the first actor has the capability to perform SIM swaps for Italian cell providers, but is now looking to expand both geographically and in the types of fraud possible with SIM swapping. A response from another actor insinuates they can help with SIM swaps to bypass two-factor authentication for consumer banking institutions. This post reflects not only the global scope of many SIM swap hackers, but also how actors move to private communication channels after initial contact.
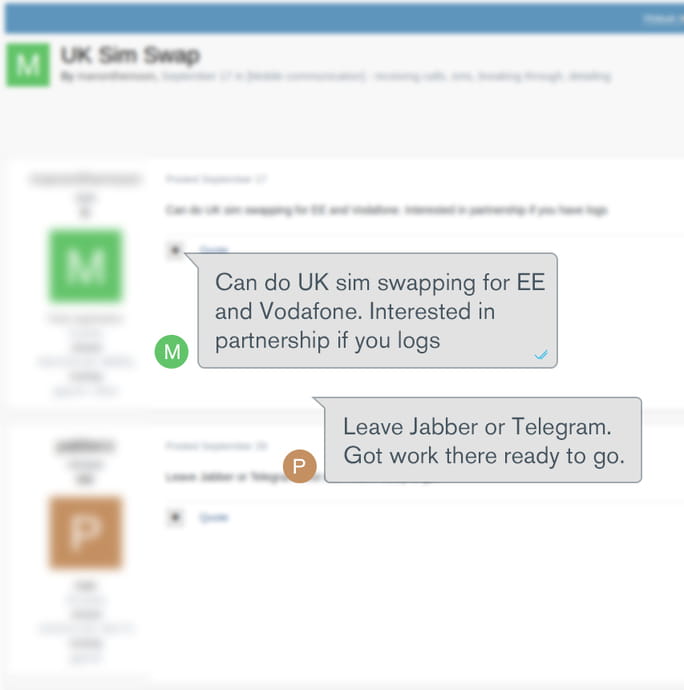
Example 2 – Actors Seeking High-Value Targets
Here we have an actor looking for a partnership with individuals who possess banking logs. They likely have the knowledge to perform SIM swaps, but not enough high-value targets. Banking logs are a hot commodity on the dark web because of the information they contain, such as PII when consumers log in, which in turn can directly lead actors to targets. A response from another actor appears to indicate they have either numbers or bank logs that can swap.
Recent Kroll Engagements Involving SIM Swapping
- A client was targeted with a high volume of spam at the same time the client’s phone service was cancelled via a SIM swap attack. On the same day the client’s SIM was swapped, an attacker gained access to the company’s corporate financial account and attempted to make a transfer.
- A SIM swap event targeted the client’s phone just before the telephone company’s physical location closed for the evening. This forced the victim to try and report the incident over the phone and prolonged the remediation time period until the victim was able to go to the provider’s physical store location when it opened again the following morning.
- Demonstrating the persistence of SIM swap attackers, a client’s phone was SIM swapped and appeared to have been quickly remediated within a matter of hours, only to find that one of the victim’s email accounts was compromised over one month later (likely by the perpetrators of the original SIM swap attack).
Kroll Experts Corner – Best Practices for Responding to SIM Swapping
Kroll Associate Managing Director Pierson Clair has a few recommendations that can forestall SIM swapping or lessen the overall severity of the attack:
Take advantage of additional online account security controls beyond SMS-based 2FA. Set up additional authentication methods or controls offered by not only your mobile phone service provider, but also the providers of all your other online accounts. These can include the use of PINs, out-of-band authentication, etc. Also, restrict the conditions under which any substantive changes to an account can occur, such as in-person only for mobile phone accounts. Other authentication options include the use of third-party applications (e.g., Google or Microsoft Authenticator).
Review your overall online security posture. Are you a person who has tended to use the same username, password, and security questions across multiple online accounts? If that’s the case, Pierson says you have made it that much easier and faster for a SIM swapper to get into your accounts and drain valuable assets. By leveraging different credentials for different accounts, you can potentially slow down an attacker long enough to give yourself the chance to notify account providers and lock down your accounts.
In the unfortunate event you do become a victim of SIM swapping, here are five critical steps you should immediately take according to a recent FBI alert:
- Report the incident in-person to your mobile service provider.
- Access your online accounts as soon as possible from a secure location or connection and change your passwords.
- Call your bank(s) and place an alert on your accounts.
- Look for unusual activity over the following weeks and months.
- Report the incident to the FBI or your local police department.
Examining Online Exposure for SIM Swapping Vulnerabilities
Successful SIM swapping schemes rely on the cybercriminal’s ability to pull together a wide variety of data points on their victims. One way people can gauge their risk (or the risk to leaders in their organization) is through an examination of their data’s exposure on both the surface web and the deep and dark web. Associate Managing Director Keith Wojcieszek explains, “Even people who believe they have been very careful sharing information online are often shocked to discover how criminals can connect disparate dots to get the information they need. For example, someone who has never shared their private telephone number online might find it has been listed in a booster club roster for their child’s school sports team that another parent posted on a social media site.”
Kroll’s CyberDetectER® DarkWeb can help examine your organization’s and key executives’ digital data profile from an attacker’s perspective. More importantly, as part of a comprehensive cyber security risk assessment, it enables you to take actions to lessens an attacker’s ability to use your data against you.
In the News: SIM Swapping
- Nine Individuals Connected to a Hacking Group Charged With Online Identity Theft and Other Related Charges – published May 9, 2019, Department of Justice, U.S. Attorney’s Office, Eastern District of Michigan, press release
- Two Men Indicted In “SIM Swapping” Scheme To Steal Cryptocurrency – published February 4, 2019, Department of Justice, U.S. Attorney’s Office, Northern District of California, press release
- Man Sues AT&T After Fraudulent Sim Swap Led To $1.8m Cryptocurrency Theft – published 10/24/19, Ars Technica
- 'SIM-Swap' Scams Expose Risks Of Using Phones For Secondary I.D. – published 10/25/19, NPR
- SIM Swap Scams: How to Protect Yourself – published 10/23/19, Federal Trade Commission
- 'Hacked' My Accounts Using My Mobile Number: Here's What I Learned – published 11/19/19, DarkReading
Sources:
1 A subscriber identity module (SIM) is a type of smart card that, among other purposes, authenticates the phone’s user to the mobile service provider.
2 “A one-time passcode or password (OTP) is a code that is valid for only one login session or transaction. An OTP is typically sent via SMS to a mobile phone, and they are frequently used as part of two-factor authentication (2FA).” Source: Idology, hxxps://www.idology.com
For further information, please contact:
Richard Dailly, Managing Director, Investigations And Disputes, Kroll Associates (S) Pte
rdailly@kroll.com